Amy Keigwin, a Digital Forensics Science major at Champlain College, presented her Capstone at the National Cybercrime Conference this year. In a nutshell, her presentation introduced law enforcement to an easier way to read the history of a computer. The Leahy Center offered her a chance to attend the Conference, and she took full advantage of it.
Today’s internet is a century ahead of the internet a decade ago. But new highs bring new lows. AAG, a cybersecurity company says one in two American internet users had their accounts breached in 2021. You read that right. The company also says data breaches, on average, cost businesses $4.35 million in 2022.
And the internet is still in its infancy! Bureau of Labor Statistics data hints the cybersecurity industry will soon burst from its cocoon. By 2031, Forensic Science Technician roles should grow 11%, and Information Security Analyst roles should grow 35%. Putting those numbers in perspective, 35% growth in ten years is seven times the national average.
TL;DR: 2021’s cybercrime numbers may look low eight years from now.
Yet many people incorrectly find digital forensics too perplexing to study. Most can’t even recognize if someone breached them. When they have to look through material like the table below to learn, who can blame them?
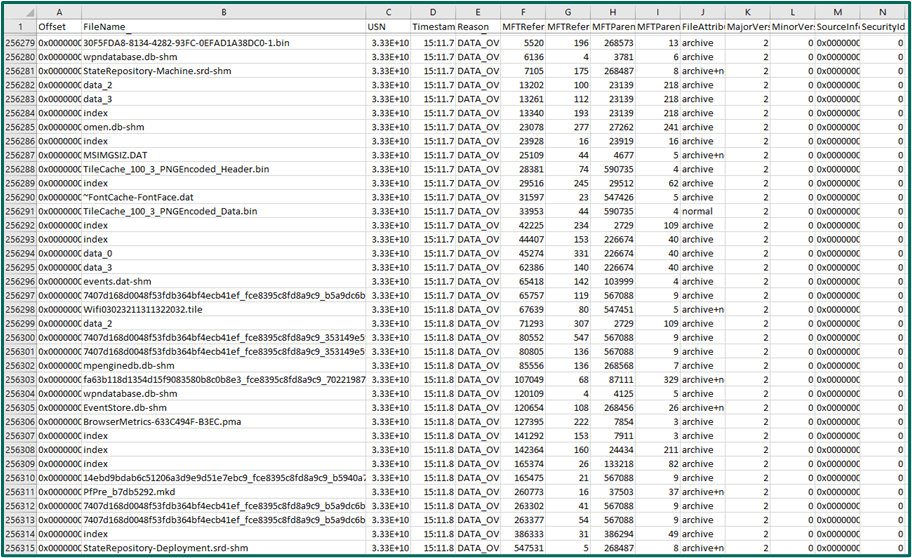
A record of file actions on a Windows computer, formatted into a CSV file.
The above screenshot is a journal file, converted to a CSV file, then opened in Microsoft Excel. As you can see, despite Keigwin attempting to make it less convoluted, the spreadsheet is overwhelming at best… Wait, you probably don’t know what a journal file is. OK, buckle your seatbelts, let’s change that.
In an interview, Keigwin herself admitted that her project is “a very technical topic and a very tricky one to understand.” The name of her project is NTFS Journal Artifact Accessibility. Here’s that title, broken down word by word.
First, “NTFS.” Modern Windows systems use NTFS, short for New Technology File System. File systems sort, store, and access files on their computer’s hard drive, and NTFS is the most up-to-date file system. Its sole disadvantage is that devices using older file systems struggle when reading NTFS files. It follows that it would be the best file system to use, opposed to older file systems like FAT or HPFS. In this circumstance, new actually does correlate with better.
“Journal” describes the journal file, which is linked to something called the Master File Table. The MFT contains info on any file ever on the computer’s NTFS file system. Yes, even deleting a file doesn’t remove its data from the table, so no, even the Recycling Bin can’t save you from your download history. The NTFS also records all file actions performed on the computer, and it does this through the journal file.
“Artifact” refers to a record of an action taken by the device. This differs from user-made content, as content is what’s in the foreground. This article is content. The journal-file-logged record that you clicked on this article is an artifact. Artifacts are also different from evidence, as not all artifacts prove that a crime happened. In Keigwin’s project, artifacts are the file actions recorded by the journal file. Anytime you move, open, create, delete, or modify files, the journal file will know.
If a cybercriminal commits a crime on a computer, the journal file would know.
Journal files are protected, too, so cybercriminals can’t easily tamper with them to warp the truth. But that doesn’t matter if law enforcement doesn’t know how to read journal files, or can’t get far enough into readings like this one to understand what a journal file even is. That’s where the “Accessibility” part comes in. Keigwin’s project took the information in the spreadsheet above and formatted it into graphs, tables, charts, and even interactive dashboards.
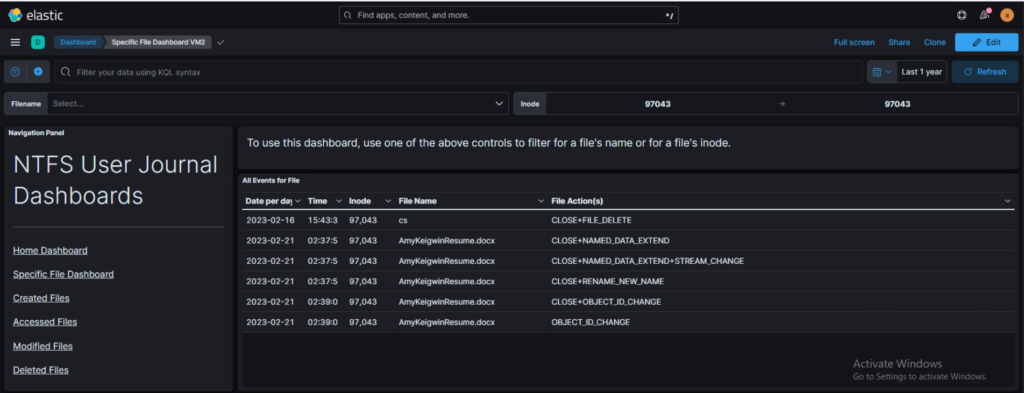
Shows “All Events for File,” that file being AmyKeigwinResume.docx.
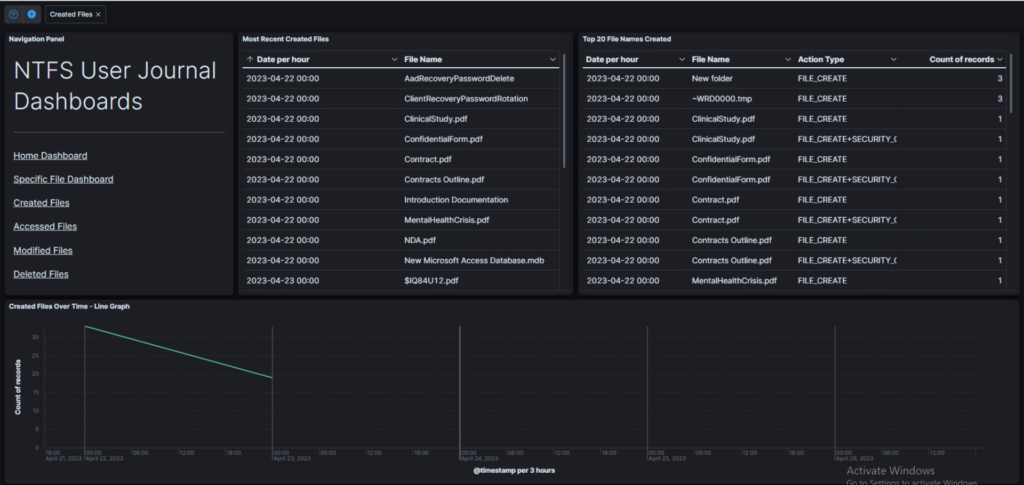
Dashboard filtering for all created files taken from the journal file.
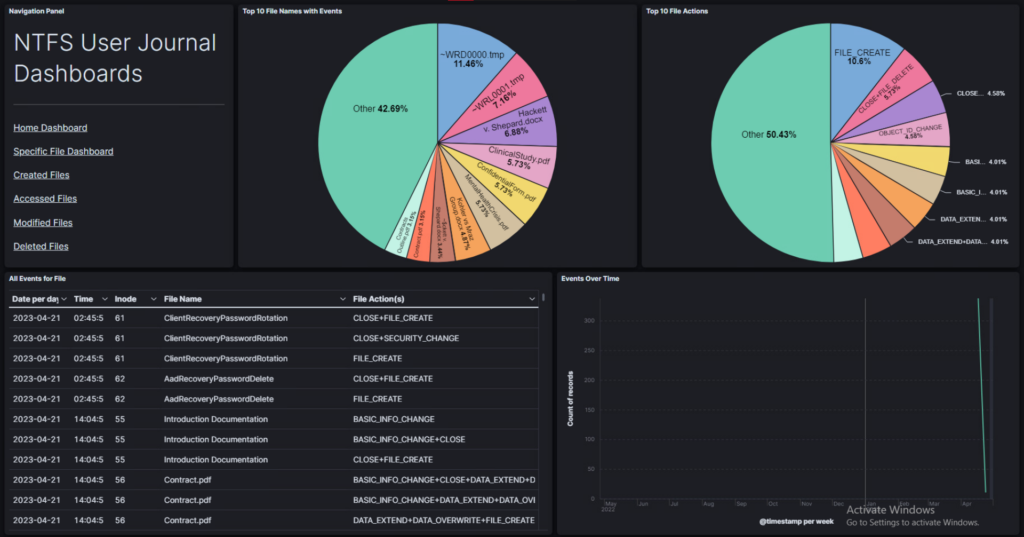
Main navigation dashboard, shows an overview of all events from the journal file.
You still need a bit of computer know-how to understand it, but there’s a clear difference. The dashboards describe files by names, actions, date and time of those actions, and their inodes. The files can also be sorted and graphed. It feels like navigating a mini journal file, which was partly the intention.
Keigwin cited ElasticStack as being critical to the project’s success. ElasticStack is an open-source software that allows users to search, study, visualize, and present data. She used the software in her role at the LC, and naturally, she found it a must-have for her Capstone.
“Leahy Center [gave] me the experience of ElasticStack and allowed me to make friends who are able to help,” said Keigwin.
She planned on improving her Capstone even further by implementing extra programming aspects, but she ran out of time. When asked about her Security Analyst Supervisor role, she praised the opportunities the Leahy Center offered her.
“I was granted the opportunity to go to this conference and present because I worked at the Leahy Center. I got a lot of education and training that was not standard to my degree program… [What I learned here] is not even really taught at Champlain, so that’s a really big skill bonus for me… [I can say,] hey, I have this experience, it’s not digital forensics, but I can make it digital forensics.”
Keigwin seized every resource available, making strides in her field before she even graduated. Going forward, she is pursuing her master’s and aims to graduate fully by the end of December.

By Briar Gagne ’26, Professional Writing
Briar Gagne specializes in technical writing and copywriting, with a strong focus in cybersecurity topics.
Sources:
https://aag-it.com/the-latest-cyber-crime-statistics/#:~:text=53.35%20million%20US%20citizens%20were,businesses%20and%20individuals%20is%20phishing
https://data.bls.gov/search/query/results?cx=013738036195919377644%3A6ih0hfrgl50&q=cybersecurity+inurl%3Abls.gov%2Fooh%2F
https://www.datto.com/blog/what-is-ntfs-and-how-does-it-work
https://www.bluematador.com/blog/what-is-an-inode-and-what-are-they-used-for
https://www.vestigeltd.com/resources/articles/digital-forensics-content-vs-artifacts-whats-difference/#:~:text=Forensic%20artifacts%20are%20items%20that,difficult%20to%20access%20and%20manipulate