Table of contents
In 2012, ASUS released the RT-N66U, a completely unprotected router. Anyone with an internet connection could access the router and any personal files on it. Despite being aware of the issue, ASUS left over 100,000 people vulnerable to cybercrime for the next three years.
In a separate case in the summer of 2011, an anonymous hacker breached the Certificate Authority DigiNotar. At that time, the company held massive power over the web. The hacker took advantage, impersonating Google.com, and using the misplaced powers of certificate authorities to create a fake Gmail at the top of all search results. This tactic allowed them steal the passwords and email addresses of over 300,000 Iranians. What they did with those credentials is unknown, as the hackers’ identity is still in question today. A strong theory claims, however, that the Iranian government hacked DigiNotar to censor their citizens’ protests over the 2009 election of Mahmoud Ahmadinejad.
Tech has been fated to become a basic need since the internet was born. Considering one in two Americans were victims of security breaches in 2021, personal cybersecurity is already a crucial form of self-defense.
Being ready to shut and lock your digital doors yourself can give help give peace of mind. That’s why I, the Leahy Center’s Tech Writer, bring you this Beginner’s Guide to Home Cybersecurity.
Here’s some bite-size advice before we dive into the fifty-course meal of how to build an invisible fortress:
The first thing to note: Just like staying physically healthy can bolster your physical self-defense, cyber-health ties into cyber self-defense. Remember to floss your teeth tonight, and remember to restart your phone before bed.
Second thing: Learning to implement cybersecurity into your life is about making it a habit. Once you know the basics, you can defend yourself. But you must be consistent, as certain practices are unsafe. For instance, you might accept website cookies, but that isn’t a healthy habit. Remember to decline cookies the same way you remember to lock your doors. I’ll admit learning some pieces can be challenging, but most times, it’s a matter of setting it, forgetting it, and resetting it. And investing in your security is always worth it.
Finally, educating yourself about your tech will go a long way. It doesn’t have to be a lot at first. Backing up your files, checking for updates, and getting better passwords will put you above most people.
Let’s begin.
Cyber Hygiene
Have any scammers called you recently? Is your email clogged with random garbage? Conversely, have you ever clicked on a shady link, even by accident? Posted anything on social media that you regret impulsing into existence?
These missteps are the online equivalent of injuring yourself; the errors hurt the computer, and the computer dies when it becomes unusable. Your computer gets sick when you interact with spam calls, click shady links, act careless on your socials, or take any action that damages your online experience.
Your computer stays healthy when regularly taken care of. Let’s look at some ways to brush your online teeth.
There’s (hopefully) a lock icon left of your URL.
Do you see it? Click on it.

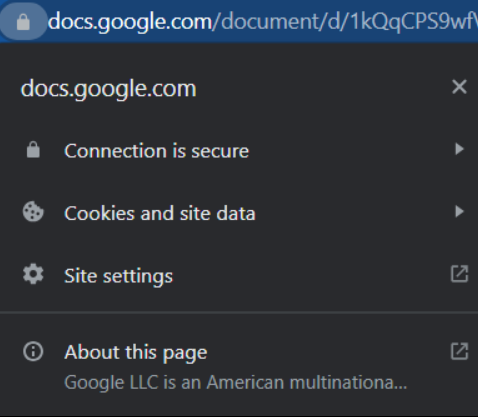
Google users should see something like this.
If you see the lock, you’re in the green. If you see the red 
Well, it involves more than just the letter s. HTTPS uses TLS, a protocol that encrypts your HTTP requests. In English, TLS jumbles communications between behind-the-scenes parts of a website. This security protects you by hiding where you’re going, what you’re up to, or any personal information you enter—important stuff.
Click on “Connection is secure,” and you should see this picture:
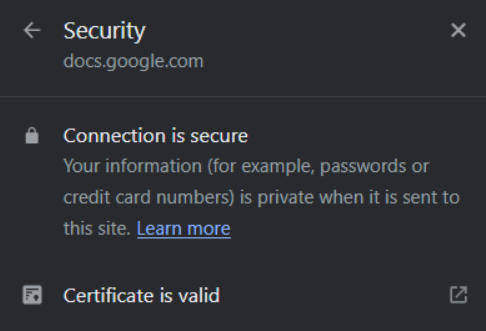
The certificate it mentions is signed by a certificate authority (CA). CAs verify the identity of websites and control what users see as fishy. That’s why the DigiNotar hack was so effective. The hacker posed as a CA and manipulated online reality itself. They effortlessly made their Gmail the trusted one and the trustable Gmail the red 
If you want to turn off cookies on all of your websites, “Cookies and site data” is the place to do it:
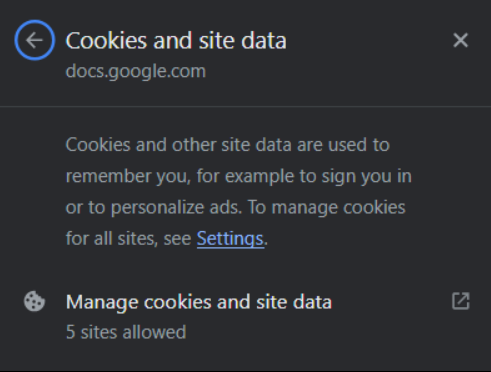
“Site settings” takes you to a vast list of permissions. It lets you block location, mic access, and camera access… once you find the settings, of course.
Click on “About this page,” and an explanation like this should pop up.
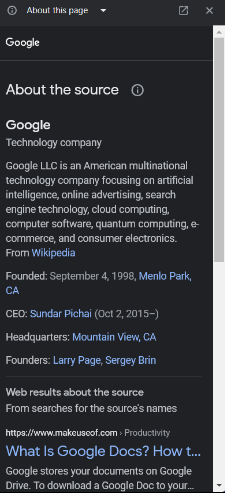
Google will send information about the page you find yourself on. This feature is handy, as the best decisions are usually the most educated.
Don’t accept cookies.
Do not be tempted. Once you stick your hand in the jar, getting it out is… pretty easy. No promises that a lot of personal data didn’t get snatched, though. Here’s how clicking the funny “accept” button breaches your privacy.
Cookies are responsible for remembering information about you. On a website with a lot of content, cookies cater your search results to what you might like. They also remember your sign-in info and passwords, all that important stuff. The choice is yours, but I don’t think a slightly more convenient experience is worth exposing your IP address.
If you click on the lock again, click “Cookies and site data,” and then “Manage cookies and site data.” You’ll see something like this.
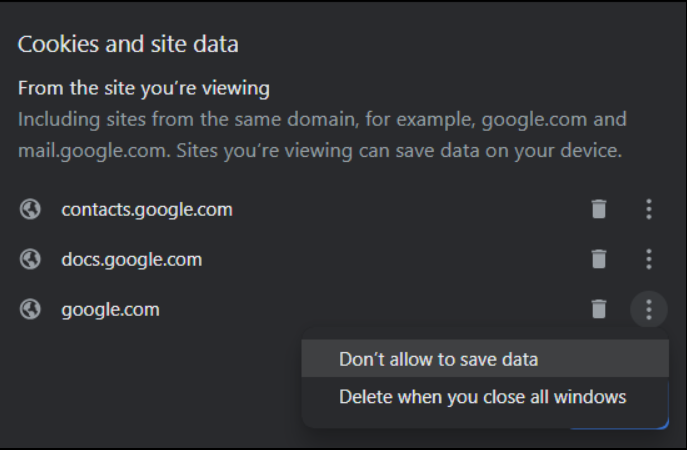
Don’t remove cookies from google.com; you’ll get an error when trying to sign in.
There should also be cookies listed from sites you aren’t viewing. You don’t see it in my picture because I cleared them all from view, mistakenly thinking the trash can remove websites from my “accept cookies” list. Click on the three dots next to a website. Then, click “Don’t allow to save data.” That will shut off cookies on the website and save you from a company knowing your IP.
Don’t interact with spam mail/calls.
Picture it: it’s your Capstone. You’ve been preparing for this for months. You step up in front of the class. “Alright,” you say. “My presentation is about-” Your phone ear-piercingly rings in your hand, and you don’t recognize the number. The caller’s name is listed as SCAM LIKELY. “Just a moment, sorry.”
You could answer the phone, put it on speaker, and subject the caller to a classroom-wide verbal attack. No way they’d call again after that, right?
Nothing is more obnoxious than letting the phone ring. But letting spam callers go to voicemail is an investment in not having them call again. Change your ringtone if that would improve your morale.
If you keep leaving them on voicemail and the situation doesn’t resolve, you may have to look into the root of the problem. Ask yourself some questions. Why are these scammers and spammers calling me specifically? Where might they be getting my number from other than a phone book?
This is tough advice for people who work on call, people who put their number in their email signature, and for the less tech-skilled elderly. Anyone predisposed and vulnerable to scam callers should look into a blocking service. There’s also the www.donotcall.gov number at 888-382-1222. The most obnoxious spammers might not care if you’re listed on that, though.
If you can help it, don’t toss your number around everywhere. It naturally follows that if you call more people, spammers think you’re more likely to answer. More likely to pass on the scam.
Don’t let fear of scammers control you, but be careful not to egg them on. It’s a tricky balance.
If spam calls are annoying you, look into it. This isn’t something you have to endure. You can cure it.
Don’t click on links.
Well obviously you can click on links. But be careful. Think: do the actions asked of you line up with the actual person or company’s motives? Even if someone claims to be from a company, or claims to be someone, think twice. Phishing people into giving up their information is easier than ever.
Someone tried to phish me recently. On Discord, a copycat profile of Mark Tilbury—the creator of a finance server I joined—sent me a friend request. I looked in the server and found that Tilbury’s account didn’t message me. The phisher asked about my financial situation.
Truthfully, I did have to think twice. It’s an unoriginal yet clever way to deceive someone. The scam becomes more dangerous when they use “evidence” to “prove” that they’re the real deal. If these phishers send you a malicious link, they could gain access to anything on your computer. Remember: links can also be downloaded, and hackers can put everything they need in a downloadable file.
Not to fearmonger, but anything could be on the other side of that link. Anything. So make sure the business you’re emailing is actually the business you’re emailing.
Ultimately, I ghosted “Mark Tilbury” like it was a sketchy first date. But that involves catfishing more than phishing fishing.
Use different passwords for different accounts.
Yeah, I’m gonna be that guy.
I’ve been guilty of this stuff, too, Don’t take it personally. Don’t use the same password over and over again. If you do, change them a little bit each time. Throw in an ! or ? or 4 at the end or beginning. Changing your passwords every year or two, if not more frequently, might also be a good idea.
Your Wi-Fi and router admin passwords should be secure and hardest to guess. They should be long and forgettable, like the auto-passwords Google recommends now and then. Make complex passwords and use a password manager setup with MFA to make your life easier. Strong passwords does not have to be an annoyance!
You could install a password manager to remember all your passwords, but that doesn’t fix the core problem. Putting your passwords on a secure app on the computer is probably safe, but it isn’t perfectly safe like not having them on your computer at all. We have yet to hit an age where hacking a piece of paper is possible. That’s coming from me, though; I am still determining what the scientists are up to in Area 51.
If you have trouble remembering, write your passwords down. Tack the papers in a hidden location near their corresponding devices, and you have a risk-free solution. With this idea, your only threat is in-person, and if a burglar breaks in, they aren’t going to sit at your desk and look for your passwords. They’re going to take your computer and run. That’s still a bad outcome, but at least they don’t get the password to your bank account that way.
That is, if you didn’t save your passwords…
That ties into my next point: keep websites from remembering your passwords. It’s a little creepy when sites I rarely go to remember me. I get a sensation of dread thinking about how the Cow Crusaders log-in’s been waiting for me for months.
Here’s a guide on how to make your crazy stalker browser forget your passwords because I don’t feel like making a guide for every different browser. I use Google, and it’s been eager to save my passwords. If you need to catch up on this stuff, feel encouraged; I also have a long road to cybersecurity.
One feature I love is Two-Factor Authentication (TFA). It could also be known as Multi-Factor Authentication (MFA). If a website offers this, use it.
Bring your mind back to the burglar story. Imagine you did save your password to your bank account. When the burglar tries to sign in, a little prompt greets them. “Please enter the six-digit code sent to your phone number.” Their little fist then greets their wall as they rage out.
That burglar’s mistake was being too old-school. They should have realized we live in an age where important stuff is usually online. That’s why cybercrime will rise. TFA protects you from cybercriminals, too. For example, if the burglar were hacking you, they’d also need to hack into your phone. That would take considerably more time and have a lower chance of success. They might reconsider hacking your account—a hands-up victory for you.
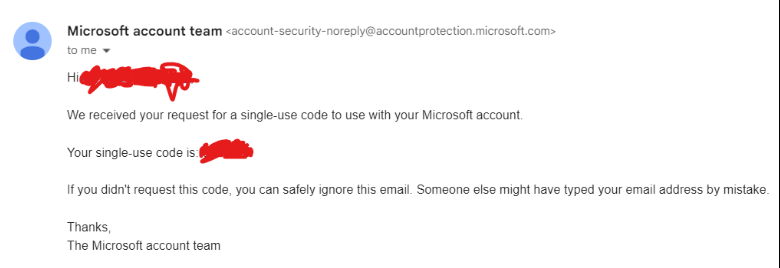
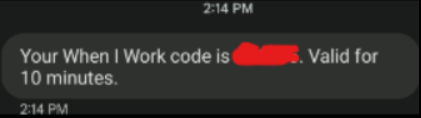
As you can see, the Microsoft code was single-use, and the When I Work code lasted 10 minutes. Even the modern-day cyber-burglar has minimal ways around single-use and expiring codes.
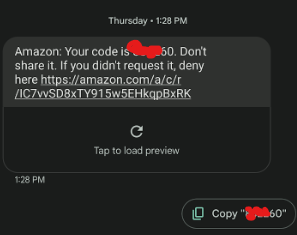
Below the Amazon code, there’s an extra bit about not sharing it. That’s a smart move by Amazon. Saying “don’t share the code with anyone” protects code receivers from spear phishing – an easy way in for the cyber-burglar. If a hacker wanted my Amazon code, they could act as an Amazon representative that “needs my code” for something. You wouldn’t think that’s convincing, but you’d be surprised. They wouldn’t put “Don’t share it” in the message if it were a bite-size issue.
Sharkbite-sized, maybe.
Be careful on your socials.
Digital permanence: the idea that what goes up on the internet never comes down.
I don’t have personal social media, so I have minimal experience in this area. I only use Discord, which isn’t the same as other platforms. When you “post” to Discord, you’re talking to a community, and you choose the scale. Posting to Facebook and Twitter is like posting to the whole world.
Information gets sent and delivered like lightspeed mail in this intense social media landscape. Around ninety-nine thousand Google searches go out every second. Count to ten, and Google’s been asked a million questions. Count to eleven, and Google has answered them all. Every minute, nearly six million people could come across your socials through Google alone.
It follows that you should be careful what you post. You aren’t safe just because you didn’t post your exact IP, home address, number, email address, or birth certificate. For instance, a photo with your mailbox in the background could compromise your street address. If you post pictures you’ve taken at shops and restaurants, someone can find the town you live in over time. You don’t need to post your town name to be exposed; Google Maps exists. And even if you don’t literally put your real name as your Facebook username, someone could easily guess the last name from the family you added as friends. If you’re streaming or sharing your screen, you could fumble the ball and leak all sorts of information. Want to pay for something? You could expose your bank account password and credit card number in one go, utterly doxxing yourself.
Most socials offer a great way around this. You can make your accounts visible to just friends. This move does two things. It takes the control away from the stalkers and passes it to you. You no longer have to worry about creeps stalking your account. Only your friends can see, so you can be open with your posts.
It’s also wise to avoid revealing the answers to account security questions. But let’s be honest, no one logs onto Facebook on their mother’s birthday and thinks, “I have to avoid revealing my mother’s maiden name today.”
Ideally, treat security questions like passwords. Instead of using your mother’s actual maiden name as the security question answer, make something up and write it down. Sites only ask security questions in times of need, so you should rarely need the false answer.
Crucial Cyber Habits
Do you think about security as you browse the web? Ever go to Walmart and disconnect from their Wi-Fi out of fear of hackers?
Yeah, I don’t either, but you get the point.
The internet is a public place. At any moment, the web is more populated than any festival, concert, or even Super Bowl that’s ever been. Other people may be simultaneously reading this article, and they could be anywhere with Wi-Fi. Being online is like walking the bustling streets of New York, New York, dropping the lack of social distancing and keeping the easily ignorable danger.
You never know when the data breach, spear phishing scam, or aggressive hack will present itself. (Yes, when, not if.) But I’m not a fan of worrying about maybes. That’s where these habits come in. Do these, and you’ll wonder how being so secure can be such second nature.
Reboot your devices.
And not just to help your electric bill. Reboots are critical for your computer’s health.
People need sleep. Without it, illness, forgetfulness, and even hallucinations are inevitable. What fun. Your computer needs rest, too, even if it’s just a five-minute micro-nap.
When your PC restarts, it clears its memory. Ongoing tasks need memory to run. So when everything you had open closes, the memory clears too.
Memory is different from storage, which holds your files. You may know memory as RAM or random access memory. When you clear RAM, the computer drops useless stuff it may have been saving. If I played Cow Crusaders earlier, didn’t X out of the tab, and left my laptop running overnight, the laptop would hold its RAM for Cow Crusaders until I returned.
Your computer is like a car. It breaks down, and repairs can be pricey. Investing in a car’s health makes it run better and keeps you safer. Be careful with it, and it’ll barely break. The better you look after it, the better off you’ll be.
Click off tabs you aren’t using. At bedtime, turn off your computer, laptop, and phone. Give all three the occasional temperature check. You can choose a time frame to inspect your hardware, but do it at least once every three months. If you need more RAM, reduce your app usage or invest in buying more. If you need more storage, it might be time for a cleanup.
Set a weekly time to reboot all your devices, including your router. Maybe Thursday night. That way, it isn’t clogging your Friday and still sets up an easy weekend.
Check for updates every Thursday, too.
You may find the update needs a restart. Save yourself a step.
It may be Tuesday for me, but I took my advice and checked my laptop for updates. Guess what the first results were.
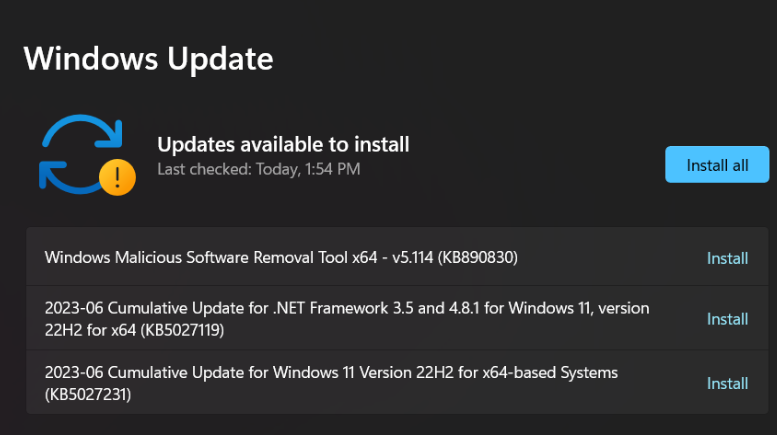
I “installed all” shortly after writing the “Restart your devices” section. Then I gave my laptop some short-lived sleep.
This one’s a no-brainer. Much of cybersecurity comes from being on the latest patch. Other than fixing bugs, there’s only a little to update besides security. Hacking a computer on Windows 7 is easier than hacking one on Windows 10. And hacking a computer on Windows 10 is easier than hacking one on Windows 11.
Users have been hesitant to upgrade to 11, though. In some cases, they have good motives. But it doesn’t change that Windows 11 is the safest it’s ever been. Your choice.
You should disable UPnP, WPS, and remote management.
Wait, wait, wait. What?
UPnP is when your network says to a new device, “Welcome to the family! Make yourself at home.” Your network then gives the newcomer access to every other device. This connection’s fine if you only have a computer, laptop, and phone. But if you have a smart fridge, smart printer, smart TV, smart car, and gaming console… Smart this, smart that. If you have those IoT devices webbed with your computer and router, the hacker won’t need to be smart to Rubber Ducky your whole rodeo.
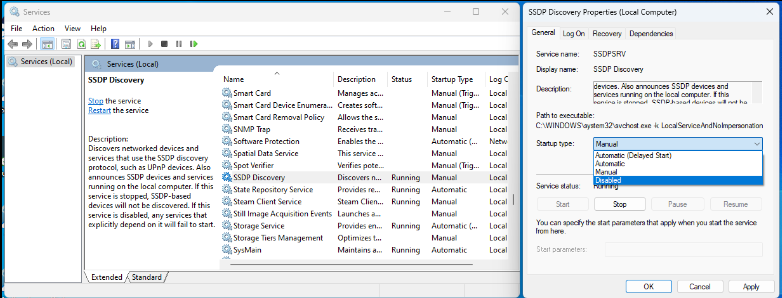
To disable UPnP, press Windows + R. Type in service.msc and proceed. Scroll through and look for SSDP Discovery. Click on that, go to Startup Type, and click Disabled.
WPS is also too convenient—but it might have upsides. It stands for Wi-Fi Protected Setup. When connecting two devices, you need to enter a password during setup. However, different devices require different steps. If you have smart devices, going to the corresponding websites and entering different passwords on each is a lot, even if you write it all down.
With Wi-Fi Protected Setup, you connect these devices by entering a PIN. Or you may have a fancy WPS button on the back of your router. Either way, WPS may be the safer option if you’re a notorious password reuser.
However, it has glaring security concerns. A hacker could brute-force attack your Wi-Fi login by entering PINs like 0000, 0001, 0002, through 9999 until it works. If you have the button on your router, you’re vulnerable to in-person hacks. It’s niche, but if you have company, someone could connect to Wi-Fi without your permission by pressing the button.
Shut off WPS when you aren’t using it. You can turn it off in your router settings. Find your default gateway and put it in a browser’s search bar to access your router settings. (DON’T DO THIS ON PUBLIC WI-FI.) Your internet provider’s login should show up, so be ready with your login credentials. And afterward, you should clear your search history.
Remote management (RM) is simple. The owner of a remotely managed device fully controls it no matter where they are.
But it’s less beneficial than it seems. Who goes on vacation and thinks, “Man, I need to change my router settings?” You’d only scramble to change your settings if you got hacked. Changing settings at that point is like driving to the airport for the flight you missed yesterday.
Remember how you got the default gateway and put it in the browser’s search bar to disable WPS? If you did that while away from home, remote management is enabled on your router. You’re vulnerable to someone else remote accessing your PC. Log on to your router settings at home using the default gateway and shut it off.
Don’t use out-of-office plugins.
If you service customers online, or secretary for a hospital, or do sales for a living, needy customers probably send you endless emails. But you have a vacation coming up. They wouldn’t email you on your well-deserved break. You wouldn’t have to reply to every email saying you’re out of commission for the next week. You wouldn’t.
Except you would. And you’ll be sighing the whole way through.
Unlike the three security hazards above, out-of-office plugins are crucial for mental health. Also unlike the above, auto-replies don’t just open doors for attackers. They jingle the jolly little bells and invite them right in.
Think about it. If you’re looking for vulnerabilities and you see
“Hello,
I’m on vacation at the moment. I will be back on mm/dd. I appreciate your patience. Feel free to contact BOSS’S EMAIL and/or call the numbers below for assistance.
MY BUSINESS EMAIL
MY BUSINESS PHONE NUMBER
COMPANY’S PHONE NUMBER”
aren’t you going to go kid-in-a-candy-store mode?
Fixing this is tricky since you need help to do it. Turn off the plugin, and you’ll get slammed with other people’s problems as you try to relax. But to turn it off safely, you temporarily need to leave the channels and remove your email from customers’ view. Gasp! You’d need to reach out to your coworkers, or worse, *shivers* your boss! And you’re not in the mood for human interaction; that’s why you’re taking the blasted vacation in the first place!
As our world becomes increasingly online, such practices will become commonplace. Young people have to be trailblazers. Even if it’s hard, we must lead the world into cybersecurity.
That got serious. Let’s talk about Walmart’s Wi-Fi.
Walmart. Houser of depressed nine-to-fivers, shopping cart over-spenders, and a tangible air of madness. Oh, and low-budget public Wi-Fi. I don’t have a source for that. It’s just… so… slow… no way they invest that much in their internet speed. It probably means they don’t invest much in internet security, either.
When it comes to public Wi-Fi, I like the food analogy. Making food yourself is always healthier because you have no idea what’s in food when you eat out. If you stroll up to McDonald’s, it’s clear there isn’t chicken in those nuggets. But restaurants could sear the vitamins out of their veggies, and you’d never know. The same is true with Wi-Fi and security. Like a restaurant salad may be faux healthy, the high-speed Wi-Fi at the coffee shop could be faux secure.
Lucky for you, you have alternatives: using mobile data or a VPN. Unlucky for you, both of those can be costly.
If you must connect to public Wi-Fi, don’t do anything risky, like going on shady websites, entering personal information, or using a work device. You know your boss might rethink that vacay if the iPad bricks.
And speaking of work devices…
There’s a saying like “leave work at work” or something. That separation’s good for mental health but also crucial for cybersecurity.
If you bring work files home or home files to work, you understand this is an issue of habit. One’s conditions affect their work, so this is more than a technical issue.
Why access home files on work devices? A personal problem or emergency could be stressing you, or you could be in a desert of boredom and need a dopamine oasis. Both are good reasons to take out your phone, as they involve your health.
It’s no different when it’s the other way around. You can resolve a case of work files on home devices by getting to the root of the problem. Are you stuck in a cycle of procrastination? Paid by salary? Work remotely and use your home computers for everything? Or maybe you don’t have two devices to separate work and home with in the first place!
When did I start sounding like an infomercial salesman…
The solution to both these cases involves talking with your boss. If it doesn’t include talking to them, see what you can do yourself. Remote workers with a laptop and a PC can segregate home files into one device and work files into the other. If you use Google Drive, make two separate Google accounts. Use one on your laptop and one on your desktop. The same goes for users of other word processors. See if you can use different email addresses too.
And yes. Both accounts need separate passwords.
Study Your Situation
It’s 1350. You’re the ruler of Scotland. You sit on your velvet throne, yawning, waiting for the Black Death to leave. Isn’t a cloud in the sky; the sun shines on the dying land. You turn towards the window, polishing your silver crown, looking over the golden grain farm. Metal boots clang against the ground behind you, but you can’t hear them. You have AirPods in.
And so, you got usurped because the guard didn’t know where the stairs were. A classic story. The only twist is the computer is the ruler, and you’re the guard.
Some companies hire hackers to attack them. But do you know why they hire hackers and not the companies that design their computers? Because the companies who designed the computers have made them as good as possible. They’d have fixed their systems if they knew of the sneaky vulnerabilities. But they can’t know, just like you can’t see the back of your neck. They need a new perspective, and hackers on the offense offer it.
To protect your PC, think like a hacker. Before your computer gets dethroned, you need to know where the metaphorical stairs are. Tech support, digital forensic investigators, and cybersecurity pros would concur: computers are complex. But learning how your computer works doesn’t have to be painful.
Most of the hard work’s already been done for you. You just have to find it.
What’s your company’s policy about being hacked?
This topic kinda leans towards the One and Dones section, but this is studying. I think.
By the end of this guide, you’ll have blown up your boss’s inbox with out-of-the-blue cybersecurity questions. Ask them if you’d get in trouble if a work device got hacked while in your possession. If they say no, then that’s great. If they say yes, you’ll have to sit there and wait out the awkward lecture about how punishing you for the hacker’s attack protects the company. You’ll have to use an eye-washing station to drown out the awkwardness, and that’s the end of your troubles.
After all, you’ll never get hacked with this guide.
Are your devices similar to the baby boomers in age?
When hardware reaches its End Of Life (EOL), it can’t run new software anymore. It may need more RAM or storage or it may be a graphics card issue. Or it could stem from an endless list of technical factors. For example, you’d struggle to run the new Zelda on a Nintendo Wii, which discontinued in 2013.
If software reaches EOL, it can’t work on new hardware; you’d also have trouble playing a game with Wii controls on the Nintendo Switch.
If a device hits EOL, it doesn’t mean the company has stopped selling it. Either way, you should move once the company stops updating your stuff.
Remember in the check for updates section when I said cybersecurity mainly involves staying on the latest patch? When companies patch security, hackers have to chase new methods. It’s not a rapid-fire chase, but they have to stay moving. Once updates stop, though, any hacking experience stays relevant. Forever.
You see how this can get rapidly dangerous. If you’re tentative to upgrade, Google your devices. Investigate new options, and see if you’d be interested in the investment.
Read the terms of service.
Don’t worry. I may ask you to change your passwords, but I’m not THAT insane.
No, I offer an easier way. Introducing: a website you should bookmark.
TOS;DR came up one morning in my Navigating Information class. Wonder why Terms of Service “agreements” are always so long? Don’t worry, I’ll show you some examples.
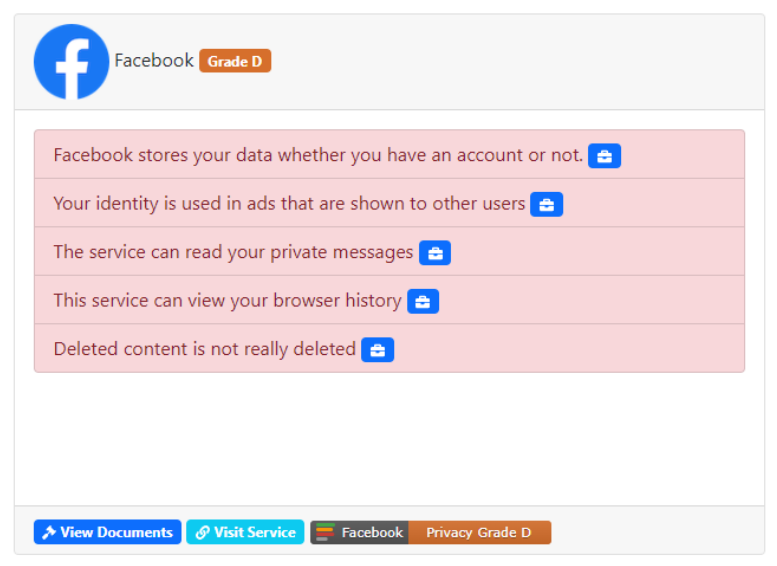
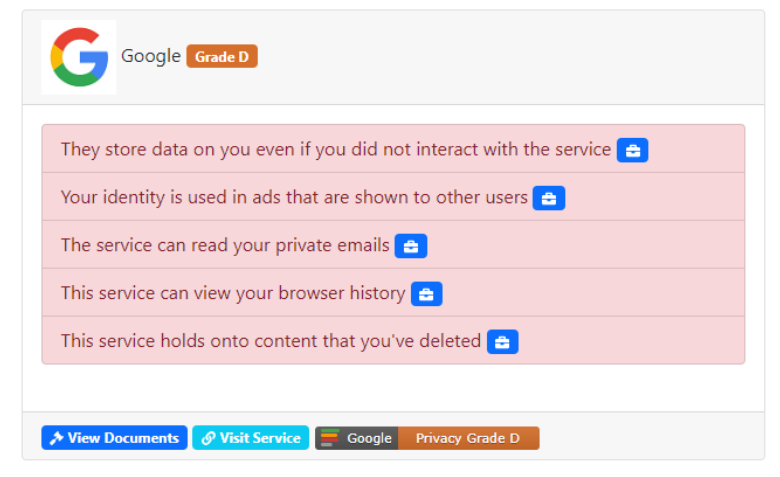
Wait, that means if I don’t even use Google, it still stores my data used on other apps? Data like my identity and location?
Bruh.
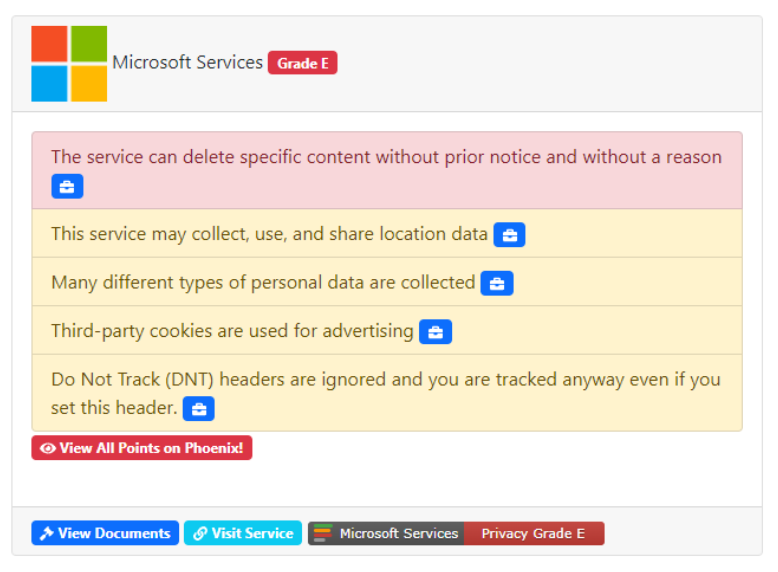
You’d never think lousy writing could be criminal till you understand what’s hidden in the Terms of Service. It’s like they hired a reverse technical writer to explain everything as poorly as possible. What kind of villain would willingly write dozens of pages of wordy BS just to deceive people?
If these risks seem OK to you, fine by me. In my class, we talked about privacy violations, and my classmate argued they had nothing to hide.
If you’re fine with the privacy breaches, keep using other sites. But if you want to be safer, take the duck pill.
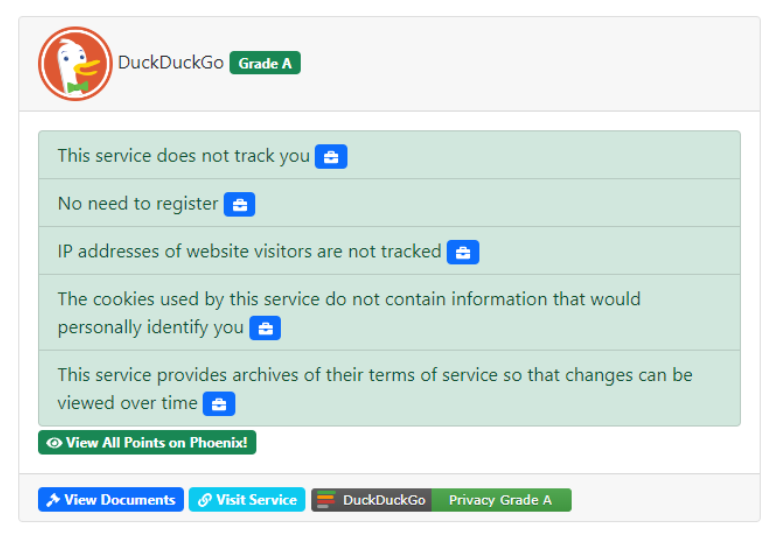
That’s right. This entire guide was one giant (UNOFFICIAL) ad for DuckDuckGo. If you haven’t installed it, you should do it now. Or don’t. Searches won’t be targeted towards you, but you’ll never be tracked again.
If you uninstall Google completely, that is.
Get familiar with how your tech works.
I’m not saying you need to double major in computer science and cybersecurity—even if both are great majors. You just need to get familiar with your devices.
A chef looks at her phone, stunned. Her smart fridge’s touch screen does many things, but she’s only used it to pull up recipes in the kitchen. She’s making chicken alfredo pizza one day, and a random number texts her address. What gives?!
It’s been a year since she got the fridge, so she forgot she set it up with the Wi-Fi. She also connected her phone during setup; the grocery list feature looked fantastic then, but it was obnoxious to set up. She never disconnected her phone, though, and she hasn’t a clue how often she’s entered her address into Google Maps since then.
UPnP and WPS connected the fridge to the rest of the network. So who knows what other data this “random number” dug up?
Hackers love people who rely on convenience. They also love people who forget their weak points. In this case, the hacker broke in because of the comfort of UPnP and the disregard for a phone being connected for no reason.
Again, it helps if you think like a hacker. To do that, you need to know where the vulnerabilities are. And to do that, you need to look into your setup. Is UPnP turned off? Are your passwords all set? Make sure you know where your network’s weak spots are. We’re about to turn them into strengths.
One Time Cybersecurity Fixes
The real devil in cybersecurity isn’t convenience, but rather ignoring the little problems. Minor issues stack up, forming dangerous openings the size of the first supercomputers. Yet those vulnerabilities are invisible because of the common convenience-first mindset.
Most people live on convenience because a security-first mindset is hard to habit. That makes one-time fixes fantastic, especially for people with virtual vendettas—the people tech support was made for.
The one time cybersecurity fixes below are like bastions, fortifying the fortress no matter how defenseless the inside is.
Secure your IoT devices.
Remember Darknet Diaries? In Episode 2, Jack Rhysider details the VTech crisis of late 2015. An anonymous hacker messed around with VTech’s website. Out of curiosity, boredom, or even hacking addiction, they launched an SQL attack on the site. SQL attacks access restricted data—when they work. And their attack worked. The hacker accessed the personal information of over 4.8 million people with a few clicks. And they got it through kids’ toys.
Gaming consoles. Printers. Google Home. All three are classified as IoT. Internet of Things is a tricky concept. An IoT device is any device connected to your network whose purpose isn’t to compute. An IoT device (like the PS5) has a specific purpose (to let you play marvelous games like Final Fantasy XVI). IoT makers design said devices for their single purpose. Big tech companies design computers to do everything.
The way I look at it, computers, laptops, and phones are the “main” devices. Anything IoT is a “side” device. The router is the heart that keeps the whole network pumping. And remember, it’s much easier to break in through a side door than through the main gate.
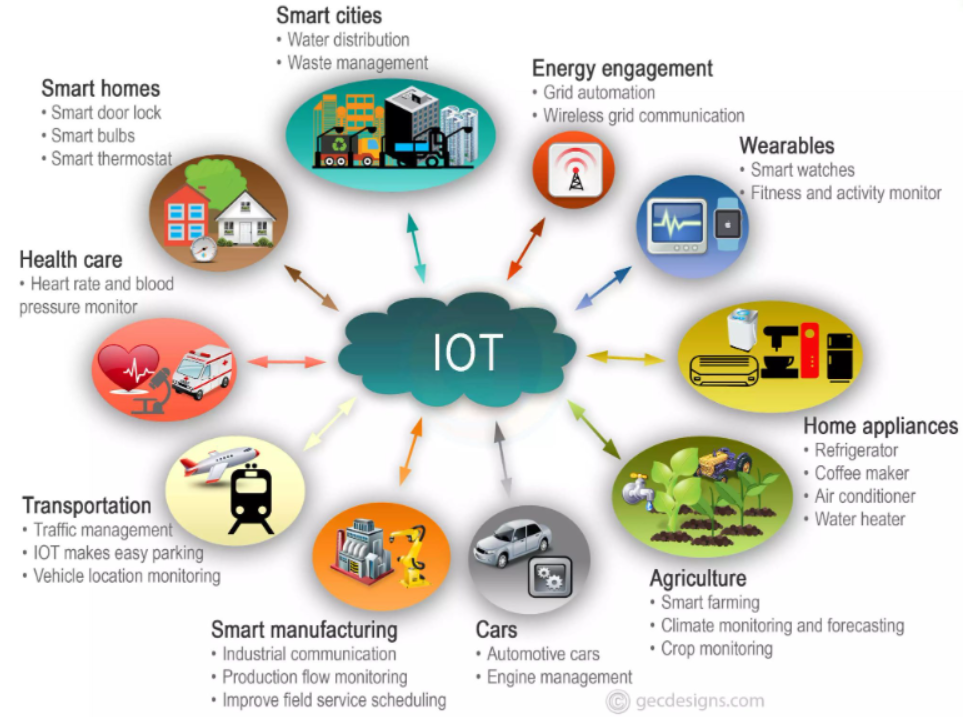
IoT describes more devices than you’d think.
First thing. Look into these devices’ login credentials. Many people keep their default passwords, which is a big mistake. Find a way to change them. If unique passwords for each device prove problematic, enabling WPS may be worthwhile. If any IoT devices offer Two-Factor Authentication options, use ’em.
Second thing. Make sure no one’s spying. It makes sense that multiple people can easily share devices meant for convenience. It makes less sense that companies can steal your data. Look at the VTech incident. Why did they need children’s data? And why were they holding onto it? And why was this data completely unsecured??? For your well-being, take an hour and update your privacy settings on every device you can think of, and then a few more. Each has a different process, so Google search some fixes for your specific models.
Third, if these devices have an automatic update feature, enable it. It makes them less hackable with one button press.
Sorry, this one’s a timesink. But you only have to do it once!
Enable Wi-Fi Protected Access 3 (or 2).
This stuff’s important, too. Many of these one time cybersecurity fixes are “modes” your computers run on. If you’re in the wrong “mode,” you’re permanently vulnerable.
The Wi-Fi Alliance (yes, that’s their actual name) created the OG Wi-Fi Protected Access to defend users against hackers. WPA3 and WPA2 encrypt data on your Wi-Fi to protect you. If you’re on an earlier build like WEP or WPA, you must upgrade to retain any chances of cybersecurity. WPA2 has encryption, but WPA3 does it better. Guessing your password is trickier in WPA3, too. The protocol also offers a safer version of WPS called Wi-Fi Easy Connect.
Yet the Alliance doesn’t require WPA3 on all devices. Unless the rules change, WPA3 won’t be mandated until 2030. On July 1st, 2020, the Alliance began requiring WPA3 for new devices to pass their certification. The bad news is they only check up on companies once a decade.
What does this mean for you? You should check if you’re on WPA2. If so, consider upgrading to a new router. You probably can’t upgrade your old router—unless you’re a turbo tech wizard.
If you can upgrade from WPA2, great, but if your device can’t support WPA3, don’t worry. WPA2 sure beats its predecessors.
Protect your router.
Again, your router is the heartbeat of this security deal. Unlike an actual heart, though, it doesn’t take cardio to keep it strong.
Changing its default SSID is a good start. An SSID (Service Set Identifier) is a Wi-Fi network’s name. If you live in a populated area, like an apartment complex, click off your Wi-Fi momentarily. Look at all the networks you could connect to. Their names are SSIDs.
Imagine you’re a hacker scrolling through that list. If you see one like “Briar’s Wi-Fi,” you won’t be too excited to hack it. But if you see ones like “TechLover42” or “ThePasswordIs789,” you’ll be a little interested.
You can still have a funny Wi-Fi name, though. Humor is always good.
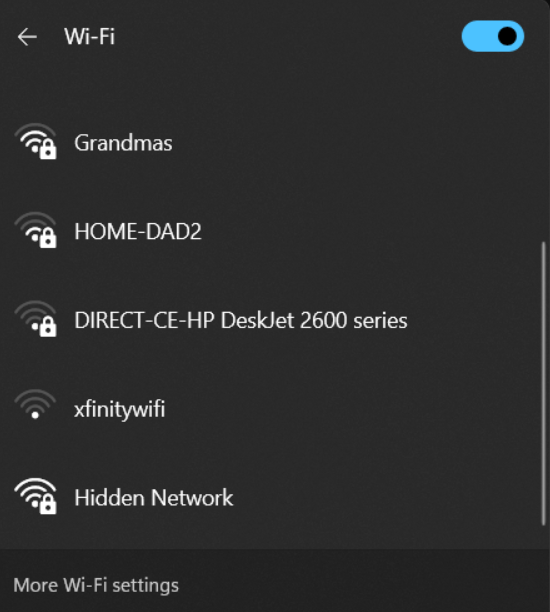
Unfortunately, the name “Grandmas” may entice hackers; older people tend to struggle with technology.
You can’t make your router password 789. Maybe 78!978978978!9789789789e7897899 would work. Write some obnoxious password down and leave the paper somewhere memorable.
Also, look into upgrading your router to IPv6. This enhancement prevents the IPv4 death of the internet. Even though IPv6 can be less secure than v4, that could change as it updates. It’s safer to be up-to-date, and you can take a step to make it even safer.
Secure an IPv6 router by enabling network address translation (NAT). NAT is a big deal, so much so that IPv4 internet doesn’t even work without it. Anytime you send data out to the internet, NAT protects you. You could Google google.com, click on a Leahy Center article, or send a bizarre tweet. In all three of those cases, just before you hit the border between your network and the web, NAT publicizes your private IP. On the return trip, it turns the IP back to private.
If your connection stayed private, your ISP wouldn’t recognize your IP when you tried to return to your network. With a permanent public connection, though, you’d be exposed 24/7.
If you’re considering investing in a new router, get one with IPv6. You can also check for it in your router settings. Remember, enter your default gateway in the browser search bar. If you can’t find IPv6 in the settings, look for specific instructions to enable it using your ISP and devices. This site will review your IPv6 security and compatibility.
BUT NO, SERIOUSLY, PROTECT YOUR ROUTER.
We’re getting to the good stuff. I take it you’ve heard of firewalls.
These handy things stop anyone and anything unwanted from going where they shouldn’t be. I talk about adding “walls” to your “fortress” all the time, but firewalls are literally a defensive wall between the public internet and your private network. They monitor outgoing and incoming traffic. They’re similar to NAT, but they outdo it tenfold on security.
Outgoing traffic is data your network sends out to the internet, and incoming is data the internet sends into your network. Monitoring outgoing is just as crucial as monitoring incoming. For instance, if a malicious worm tries to infect another computer, the firewall exposes its presence and stops you from infecting others.
Firewalls also monitor how devices on your network interact with other devices. Two types of interaction are connectivity and communication.
Connectivity is how devices connect. A phone charger capable of connecting to other devices like controllers has good connectivity.
Communication is how devices exchange information. This exchange includes when you go to a website. Here’s what your computer does every time you click on links like this one. Basically, your computer connects to the IP of the site you’re going to. Requests and granted permissions are ping-ponged back and forth between the two. Eventually, your computer gets the permissions needed to pull up the website.
For example, cowcrusaders.com. Click on it, and you’ll get a DNS_PROBE_FINISHED_NXDOMAIN error. This happens because the necessary IP address to pull up the site doesn’t exist. The site cowcrusaders.com doesn’t work because Cow Crusaders isn’t real.
Deploy the network segmentation. Divide the network now.
Make multiple Wi-Fis: a home one, a guest one, and IoT one.
Imagine this: You’re holding a family gathering at your house. Your cyber-clueless grandpa connects his malware-infested phone to your guest Wi-Fi. Your other guests might be the victims of some cybercrime contagion! “How unfortunate,” you say, sipping your wine. You’re connected to your separate and unaffected home Wi-Fi. “How unfortunate indeed.”
Separating your IoT devices adds another layer of security. Putting the IoT stuff on a separate network removes the chance of hackers blipping from your smart car to your PC. Dividing the network also speeds up your devices. When everything’s clogging the home Wi-Fi, it’ll be slower than splitting the devices into three Wi-Fis.
Here’s a video guide on how to set up guest Wi-Fi for a specific router. Go into router settings, and if the steps in the video don’t work for you, Google what the solution is for your particular router. If there aren’t any videos, look into solutions for how to add guest Wi-Fi on your provider’s routers, as what works for one Xfinity router may work for another.
Install security software.
Antivirus software does some important stuff. It monitors your computer’s incoming and outgoing traffic, checking any data sent to you and any data you send. An antivirus automatically scans your computer to check for threatening, malicious files. You can run the scan manually, too. Either way, once the antivirus finds one, it deletes it.
But how can it differentiate between the threats and your poor, innocent files? Well, the antivirus looks for patterns found in malware. It takes care to identify these patterns before deleting anything.
Malware refers to any malicious software, including viruses, worms, Trojans, spyware, or any other threatening software. Viruses and worms both pose significant threats, despite spreading differently. A virus spreads via user interaction with a file, whereas a worm spreads on its own, infecting devices on the same network as its host. Trojan horse programs pose and run as standard programs, but in the background, they steal any data you enter. And if you want to be spied on, you could install spyware on your phone, granting hackers info and even control over parts of your life.
Well, isn’t that just rainbows and sunshine?
Here’s the part where I suggest which antivirus to install. First, I recommend which ones not to install.
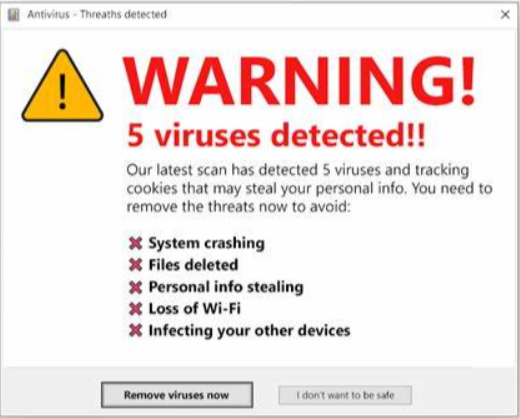
I tried to click “Remove viruses now,” but the tiny people living in my computer won’t let me. No escaping the “Threaths detected.” Guess they’ve already hacked me, lol. “Our latest scan” came too late… Wait, who is “our??”
I’m not even going to be sarcastic. Don’t click pop-ups like the picture above.
If you want a real antivirus, I’d recommend trying Bitdefender’s free plan. It’s rated as highly as some paid plans. Bitdefender’s paid plans are some of the best, priced at $25 annually. But you should try the free version first. See if it works for you before making that investment.
If it does work for you, Windows Defender is also a good option. For $36 a year, up to 300 users can protect five devices each. That means you can defend up to 1,500 devices for $3 a month! Microsoft’s site calls it “enterprise-grade, next-generation antivirus protection,” which means it’s fit to protect even the largest enterprise businesses.
Look into an antivirus browser extension, too. Bitdefender also has a plugin called TrafficLight. It tells you if cookies breach your privacy or if you’re on a risky website. Although most risky sites have the red 
How secure is your email?
Remember that lock icon, all those words ago? Recall how it uses TLS? That stands for Transport Layer Security. It encrypts incoming and outgoing data and triple-checks said data for malicious alterations. It also makes sure those exchanging the data aren’t imposters.
You can check the security status of a specific email. In Gmail, click on the small arrow under the email sender address and right of “to me.” In Outlook, go to File, then Properties in the selected email. Google it if you use something else.
Speaking of something else, consider moving to a secure-er email provider. Swapping over from your current email can net you end-to-end encryption and minimized metadata. Providers without end-to-end encryption don’t encrypt emails server side, so they can technically read your mail. Gmail even stores the time and date that you send emails.
Look into providers like ProtonMail, Tutanota, Mailfence, and even Posteo if you feel fancy. ProtonMail’s servers are in Switzerland, Mailfence’s are in Belgium, and the other two’s servers are in Germany. If you care about distance from the servers, there it is.
If you install, you have to use ProtonMail’s and Tutanota’s dedicated apps. Posteo is the only provider with a required cost, but it has extra benefits like supporting PGP and not requiring you to enter personal info.
Make your selection wisely. You only have to move providers once, but your choice holds the impact of a consistent habit.
At the end of it all… the VPN section!
You’ve almost escaped my nagging. Keep pushing!
VPNs are great. It’s like a cybersecurity bundle, condensing many solutions to the abovementioned troubles into one package. Why, it’s such a miracle solution, I expressly saved it for the end so you’d keep reading. You can thank me later after I tell you how VPNs work.
Privacy, anonymity, and security are all benefits. VPNs hide your location, letting you bypass government censorship. (Some countries don’t like that. Here’s a list of them.) You can even save money by online shopping anywhere in the world. VPNs encrypt your connection, keeping you safe on public Wi-Fi. It uses an encrypted tunnel, which hides your data and IP address.
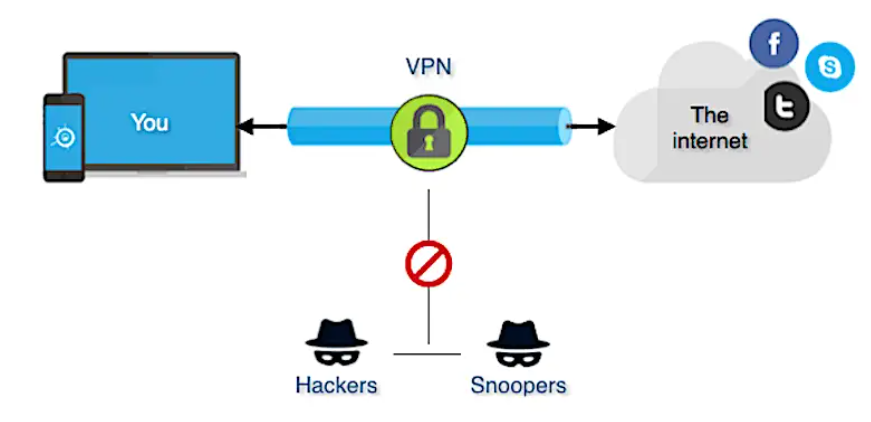
No intruders are invited to YOUR encrypted tunnel.
So, there are free VPNs available. Sometimes, they’re as good as the paid stuff.
SurfShark is a great VPN on a budget, even if there’s no beating free. It’s about $13 for a monthly subscription, but buy a two-year plan, and the price plummets to $2.30 a month. There are some security issues, but it’s lightning-fast.
NordVPN is $12 when paying monthly but $3.50 per month on the two-year plan. It isn’t as fast as SurfShark, but it’s a great all-rounder worth the price.
ExpressVPN costs $13 for monthly payments, and their yearly plan is $6.67 per month. The higher price pays off in everything except speed. This VPN’s the way to go if you only care about security and no other factors.
Lastly, ProtonVPN offers a free plan, yet doesn’t limit free users’ data usage. It has fewer server locations, yet it’s still rapidly quick. An excellent choice if you’re getting into VPNs—and if you’re new to cybersecurity.
Stay up to date with Twitter, Instagram, Facebook, and LinkedIn so you always know what we’re up to!

By Briar Gagne ’26, Professional Writing
Briar Gagne specializes in technical writing and copywriting, with a strong focus in cybersecurity topics.
Sources:
Image by rawpixel.com on Freepik
The Latest Cyber Crime Statistics.
HTTP vs HTTPS: What are the differences?
Should you accept cookies? 5 times you definitely shouldn’t.
National Do Not Call Registry.
Computer Security Resource Center Glossary.
How to remove a saved password from a web browser.
The Leahy Center for Digital Forensics and Cybersecurity.
10 Big Reasons Not to Upgrade to Windows 11.
Windows 11 Is Much More Secure Than Windows 10: Here’s Why
Apple announces macOS Sonoma at WWDC 2023.
What is UPnP and why you should disable it immediately.
What is Wi-Fi Protected Setup (WPS)?
Psychology: Why boredom is bad… and good for you.
Terms of Service; Didn’t Read.
Evolution of Hardware (1940s-now)
Teen hackers study considers link to addiction
Are You Using IPv6 Yet? Should You Even Care?
What Happens When You Visit a Website?
How to Remove Windows_Firewall_Alert Pop-up scam
IPV6 vs IPV4: what’s the difference and which is most secure?
IPv6 Security Guide: Do you Have a Blindspot?
How to Set up a Separate Guest Wi-Fi Network
Bitdefender Antivirus Free Download
Bitdefender TrafficLight Free Download
Are VPNs legal? Country guide for 2023
What is WPA3, and How Do I Get It On My Wi-Fi Router?
(Definition of) Virtual Private Network (VPN)
What is IoT? & Role of IoT in digital marketing
Honorable Mentions
cowcrusaders.com